You might know that DevSecOps is all about security measures in the software development process, but how should it look in practice? How can you use it to create a secure CI/CD pipeline? What are the main DevSecOps phases? What is the definition of DevSecOps? And which tools should you use in a typical Dev Sec Ops pipeline? In this article, we will answer these questions, we will discuss the secure pipeline in detail, including its benefits, components, and best practices for implementing it. We will also provide case studies of companies that have successfully implemented the DevSecOps pipeline.
Cyber Threat Scenario
Let’s you own a hypothetical software development firm. You’re proud of your team of talented developers using cutting-edge technologies and generating innovative ideas. One day, however, disaster struck. The company fell victim to a cyber attack, and its systems were breached by a group of hackers. The hackers stole sensitive customer information, including personal and financial data, and brought the entire company to its knees.
In the aftermath of the attack, the company struggled to recover. Your reputation was tarnished, and your customers lost faith in your ability to protect their information. The company’s finances took a hit, and many employees were left without jobs.
This scenario is not that outlandish. Around 60 % of small businesses go down within 6 months after being hacked. That’s why it’s crucial to learn this valuable lesson. You’d better start working on creating a comprehensive security plan to protect your systems, your data, and your customers.
Start educating your employees on the importance of security. Implement best policies and procedures to ensure that all employees follow best practices when it came to protecting sensitive data. Invest in cutting-edge security technologies, including firewalls, intrusion detection systems, and advanced encryption methods.
Over time, your efforts will be paid off. When your systems are secure, your customers will be confident that their information is safe. Implementing security measures is crucial for any business that deals with sensitive information. Cyber attacks are a real threat, and they can have devastating consequences. But with the right approach and the best security measures in place, you can protect your data and your customers.
What is DevSecOps Pipeline?
If you’re unfamiliar with the concept, it may seem too complex and even scary at first. Cynics may even say it’s the perfect way to add even more complexity to your already complex tech processes. Who needs simplicity and efficiency when you can have a pipeline that’s so convoluted, it requires a whole new set of skills just to navigate it?
Just think about all the extra steps you get to take to make sure your code is secure. Plus, who doesn’t love waiting for those security scans to finish before moving on to the next step? It’s like a fun game of “will this pass or fail?” every time!
And let’s not forget the joys of collaboration between developers, security experts, and operations professionals. Clear communication? Never heard of it. Instead, you have misunderstandings at every turn. It may look like a game of telephone, but with your codebase.
If you think that DevSecOps Pipeline is the ultimate solution for anyone who loves to add extra layers of complexity and chaos to their tech processes, likes playing a never-ending game of whack-a-mole, except the moles are your code vulnerabilities and they just keep popping up no matter how many times you hit them, we suggest reading this article. You may change your mind about the topic.
In reality, DevSecOps is the best way of integrating security measures into every step of the software development life cycle. The traditional approach to software development, which involved developing software in silos by different company departments or outsourcing contractors and then handing it off to the security team for testing, is no longer sufficient in today’s fast-paced, agile environment. Developers and operations teams need to work together to ensure that security is built into every step of the development process.
The Basics of DevSecOps Pipeline
DevSecOps pipeline is an approach to software development that integrates security into the DevOps workflow. It is based on the principle that security should be built into every phase of the development process, from planning and design to coding, testing, and deployment. Take a look at a typical DevSecOps pipeline diagram:
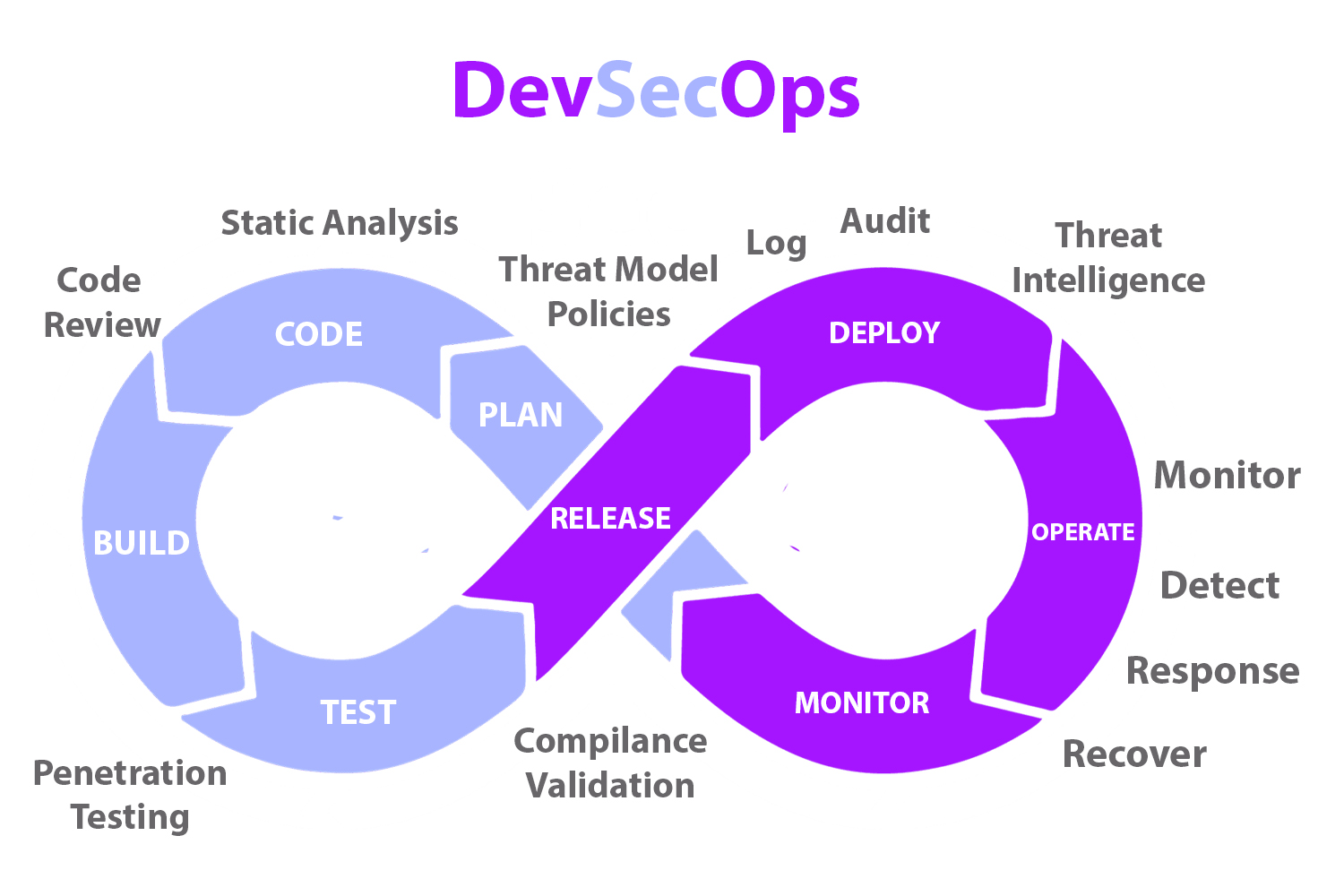
Picture this: you’re the captain of a ship sailing the vast ocean of software development. You have a skilled crew of developers, operations personnel, and security experts all working together to ensure a smooth voyage. But what if we told you that you could make your journey even smoother with the power of DevSecOps?
With DevSecOps pipeline architecture, you can spot any lurking sea monsters early in the journey, when they’re still small and easy to handle. This means you can save time and money by avoiding any costly detours or battles with larger, more dangerous beasts later on.
Not only that, but with the magic of automation, your crew can focus on more important tasks, like charting your course and making sure your ship is running smoothly. This means you can cover more ground and reach your destination faster, all while keeping an eye out for any potential threats.
And let’s not forget about the benefits of better collaboration between your team members. With DevSecOps, everyone is working together towards a common goal, making it easier to communicate and share ideas. It’s like having a well-oiled machine, where everyone knows their role and works seamlessly together.
But perhaps the most important benefit of all is that security becomes a shared responsibility across the entire crew. No longer is it just the responsibility of a few security experts – everyone on board is responsible for ensuring the safety and security of your journey.
So what are you waiting for? Set sail with DevSecOps and discover the true potential of your software development journey.
Components of DevSecOps Pipeline
DevSecOps pipeline is made up of several components, each of which plays an important role in ensuring that security is built into the development process.
Source Code Management (SCM)
Source code management is one of the most crucial components of a DevSecOps pipeline. It involves the use of a version control system to manage changes to the code base. This allows developers to collaborate on code, track changes, and roll back to previous versions if necessary. The most common SCM tools are:
- Git
- SVN
- Mercurial
Continuous Integration (CI)
Continuous integration is a process in which developers integrate code changes into a central repository on a regular basis. The code is then automatically built and tested, and any issues are identified and resolved immediately before they cause more serious problems. This process ensures that the code is always in a working state and that any issues are identified and addressed early in the development process. Popular CI tools include:
- Jenkins
- CircleCI
- Travis CI
Continuous Deployment(CD)
Continuous Deployment, or CD for short, allows you to effortlessly deploy your code changes to production. The process allows automating the way code goes through the build, testing, and deployment process all on its own, with minim-to-none human intervention.
With CD, you can say goodbye to the days of manual deployments and the risk of human error that comes with them. Instead, you can rest assured knowing that the process is fully automated and any issues are identified and addressed before the software is released to production.
It’s like having a personal assistant who takes care of all the mundane tasks so you can focus on the more important things. CD tools work tirelessly in the background, ensuring that your code is always in a releasable state and that deployments are consistent and repeatable.
CD is not just a tool, it’s a mindset. It’s about embracing a culture of continuous improvement and constant feedback. With CD, you can deliver software faster, with higher quality, and with less risk. It’s a game-changer that can transform the way you develop and deploy software.
Some popular CD tools include:
- Octopus deploy
- Argo CD
- Harness
Security Testing
Just like a secret undercover operation, security testing is the stealthy and strategic process of identifying any hidden vulnerabilities that could pose a threat to the software’s security. It’s a tireless part of the DevSecOps pipeline constantly scanning the code for any potential breaches.
Security testing can be conducted using different techniques, from the classic method of manual testing to the modern approach of automated testing. Just as a master thief would carefully analyze every aspect of a building’s security system, static code analysis, dynamic application security testing (DAST), and software composition analysis (SCA) are the tools that security testers use to assess the software’s defenses.
These techniques help testers identify potential security flaws such as cross-site scripting, SQL injection, and buffer overflows. Like a skilled detective, security testing allows developers to anticipate and thwart any malicious intent before it becomes a serious threat.
In the end, the software emerges as a fortified fortress, ready to stand up to any attacks. Security testing relies on precision to ensure that the software is well-equipped to handle any security issues that may arise.
For this purpose, you can use such tools as:
- SonarQube
- Veracode
- Checkmarx
Infrastructure as Code (IaC)
Infrastructure as Code is the practice of managing infrastructure using code, rather than manual processes. This involves creating scripts or configuration files that define the desired state of the infrastructure, which can be version-controlled and automated. Popular IaC tools include:
- Terraform
- Ansible
- Chef
Containerization
Containerization involves packaging an application and its dependencies into a lightweight, portable container. Containers can be easily deployed across different environments, making it easier to scale applications and maintain consistency. Docker is the most widely-used containerization tool.
Monitoring and Logging
Monitoring and logging are essential for detecting and diagnosing issues in production environments. To monitor and analyze application and system metrics, logs, and alerts, you can use such tools as:
- Prometheus
- Grafana
- ELK Stack
Security in Design
Security in design is the practice of designing software with security in mind from the beginning. This involves identifying potential security risks and designing the software to mitigate those risks. For example, suppose the software requires users to enter sensitive information, such as credit card or social security numbers. In that case, the software should be designed to encrypt that information to protect it from hackers.
Implementing DevSecOps Pipeline
Challenges
If you want to boost your organization’s efficiency, security, and collaboration, then you need to get on board with DevSecOps pipelines. These practices can help you deliver lightning-fast software, rock-solid security, and seamless teamwork between development and operations teams. But let’s not kid ourselves, there will be some challenges to overcome along the way. Don’t worry though, with a little bit of grit and determination, you can conquer any obstacle that comes your way.
1. Cultural Shift
You need to be prepared for a major cultural shift. The truth is, DevSecOps demands a continuous and collaborative approach to software development and deployment, which can be a major challenge for organizations that are used to working in silos. But this is one of those challenges that can be and should be overcome. To make DevSecOps work, you need to break down those barriers and create a culture of collaboration and shared responsibility. When everyone is on the same page and working towards the same goal, amazing things can happen. So don’t let a little cultural shift hold you back from realizing the full potential of DevSecOps.
2. Tooling Integration
Another challenge of implementing DevSecOps is integrating the various tools and technologies required to support the software development pipelines. This can include integrating source code management, continuous integration/continuous delivery (CI/CD) tools, security testing tools, and infrastructure-as-code (IaC) tools. Ensuring that these tools are properly integrated and working together can be complex and time-consuming.
3. Security Skills Shortage
DevSecOps requires a strong focus on security, which can be challenging for organizations that lack security expertise. This can lead to a skills shortage, with a lack of qualified security professionals available to oversee the security aspects of the pipeline. To address this challenge, organizations may need to invest in training and education for their existing staff, or consider partnering with external security experts.
4. Compliance and Regulation
Many industries are subject to strict regulatory and compliance requirements, which can make implementing DevSecOps more challenging. Compliance requirements may include ensuring data privacy, maintaining audit trails, and demonstrating compliance with industry standards. Organizations need to ensure that their DevSecOps pipeline meets these requirements, which can add additional complexity and cost.
5. Legacy Systems and Applications
Finally, legacy systems and applications can pose a challenge to implementing DevSecOps. Legacy systems may be difficult to integrate with modern tools and technologies, or may not be designed to support a continuous delivery approach. This can make it challenging to fully automate the pipeline and achieve the desired benefits of DevSecOps.
Organizations need to address these challenges in order to successfully implement DevSecOps, including fostering a collaborative culture, integrating tools and technologies, addressing security skills shortages, complying with regulations, and managing legacy systems and applications.
How to Improve Collaboration in Your Team?
If you want everyone in your organization to cooperate better, just force them to work on group projects, even if they hate each other’s guts. It doesn’t matter if the project is completely irrelevant to their job description or if they have no interest in it whatsoever. Just make them do it. That’ll bring them closer together.
And don’t forget the team-building exercises. Because nothing screams “collaboration” like playing trust games with your coworkers. Blindfolded, you must trust that your colleague will catch you before you hit the ground. And if they don’t? Well, it’s all good fun, right?
Also, you may consider the open office concept. Why have walls and doors when you can have a shared workspace where everyone can see and hear each other? And those who want to escape constant distractions and interruptions can just wear headphones listening soothing music.
If all else fails, just force your employees to socialize outside of work. Schedule mandatory after-work drinks and make sure everyone attends. Because if they don’t want to be friends with their coworkers, they’re obviously not team players.
In conclusion, if you want to create a collaborative culture in your organization, just force it upon your employees. They’ll thank you for it…eventually.
Best practices to follow to ensure success
There are some DevSecOps steps that organizations can take to ensure success.
1. Automate Everything
In all of the phases of DevSecOps pipeline, automation is an absolute game-changer. By automating key processes like development, testing, and deployment, organizations can slash the time and money it takes to develop software, while also ensuring that security is baked into every single step of the process. It’s a total win-win situation that you don’t want to miss out on. So if you’re ready to streamline your development process and level up your security game, automation is the way to go.
2. Create a Culture of Collaboration
DevSecOps pipeline requires collaboration between development, operations, and security teams. To create a culture of collaboration, organizations should:
- Foster open communication between teams
- Encourage cross-functional teams
- Provide training and resources to help teams understand each other’s roles and responsibilities
- Reward teams for working together to achieve common goals
- Implement Security Testing Early and Often
To ensure that security is built into every step of the development process, organizations should implement security testing early and often. This includes using DevSecOps pipeline tools such as static code analysis, dynamic application security testing (DAST), and software composition analysis (SCA) to identify and mitigate security vulnerabilities.
Use Secure Coding Practices
Secure coding practices are essential for building secure software. Developers should be trained in secure coding practices and should follow coding standards such as OWASP Top 10 and CWE/SANS Top 25.
Case Studies
Many well-established companies have successfully implemented the DevSecOps CI/CD pipeline in their operations. Here are some of the most prominent DevSecOps pipeline examples:
Netflix
Netflix is a streaming service that uses DevSecOps pipeline to ensure that its software is secure and reliable. The company has a team of security experts who work closely with developers and operations teams to identify and mitigate security vulnerabilities. Netflix uses tools such as static code analysis, DAST, and SCA to automate security testing and ensure that security is built into every step of the development process.
Capital One
Capital One is a financial services company that has implemented DevSecOps pipeline to ensure the security of its software. The company uses automation tools to speed up the development process and ensure that security is a priority at every step of the way. Capital One also employs a security team that works in cooperation with developers and operations teams to identify and mitigate security vulnerabilities.
Aim at the Future
As the world advances, so too does the art of software development. The future is a canvas yet to be painted, a world yet to be explored.
Software development has come a long way since its inception, and the future promises even more innovation. Imagine a world where software not only understands what you want but anticipates your needs before you even know them. Where machines work in tandem with humans to create software that is not just functional, but intuitive and immersive.
The future of software development is not just about writing lines of code, but about creating experiences that transform the way we interact with technology. It’s about understanding the nuances of human behavior and incorporating that into software design. It’s about creating software that is accessible to all, regardless of ability or language.
Artificial intelligence and machine learning will play a critical role in the future of software development. With the ability to analyze vast amounts of data, machines will be able to identify patterns and trends that humans may miss, leading to faster and more efficient software development.
In the future, software development will also be more decentralized and collaborative. Teams will work together, sharing code and ideas in real-time, regardless of their location. The rise of open-source software will only accelerate this trend, leading to a more transparent and inclusive development process.
As we move forward, the future of software development is limited only by our imagination. The possibilities are endless, and the potential for innovation is limitless. Let us embrace this future, and create software that not only solves problems but inspires and delights us in ways we never thought possible.
Conclusion
DevSecOps pipeline is a groundbreaking methodology for software development that fuses security into the heart of the DevOps workflow. This forward-thinking approach allows organizations to identify and eliminate security vulnerabilities at the earliest stages of development, saving valuable time and resources.
By incorporating security into every facet of the development process, teams can reduce the need for costly security testing later on and establish a culture of collaboration. This ensures that security is a shared responsibility across the organization, fostering a sense of teamwork and cooperation.
To put DevSecOps pipeline into practice, organizations should prioritize automation, cultivating a culture of collaboration and implementing security testing from the outset. By using secure coding practices, organizations can build top-tier software that meets the demands of both their clients and stakeholders.
Adopting the best practices of DevSecOps pipeline is the key to unlocking the full potential of software development, ensuring a streamlined, secure, and high-quality process. With this groundbreaking methodology, organizations can stay ahead of the curve and deliver exceptional software solutions.